There are several SSH clients available on Windows. Many, but not all installations of Windows 10 or 11 include OpenSSH, the same software you might use to SSH from macOS or Linux. PuTTY is another popular option amongst our users. PuTTY is an SSH and telnet client, developed originally by Simon Tatham. PuTTY is open source software and is developed and supported by a group of volunteers. Recent versions of Windows include an SSH client with PowerShell so you can connect to the NIH HPC systems without downloading or installing anything.
OpenSSH
Current builds of Windows 10 include OpenSSH by default, although it may be disabled.
The general form of the ssh command to connect to any host is: ssh [username@]host.
You can open a PowerShell window from the Windows Start Menu. In the PowerShell window, type:
ssh $env:username@biowulf.nih.gov or ssh $env:username@helix.nih.gov to start an ssh session to Biowulf or Helix respectively.
Note: The general form of the ssh command does not require a username; instead, OpenSSH will automatically fill in your system username.
However, on Windows Machine, your system username includes a domain name which is prepended to your NIH username.
The system username used by OpenSSH will not match your Biowulf and Helix username.
To avoid this problem, specify your NIH username or use $env:username when connecting to Biowulf or Helix using PowerShell.
When first connecting to a new server, ssh will report that the server's
host key is not known. It will present the fingerprint of
the host key. If the fingerprint matches one of the fingerprints shown above it is safe to answer "yes" and store the
key. Some clients are configured to reject unknown keys outright. In that
case you can include -o StrictHostKeyChecking=ask.
PS C:\Users\myuser> ssh $env:username@biowulf.nih.gov
The authenticity of host 'biowulf.nih.gov (128.231.2.9)' can't be established.
ECDSA key fingerprint is SHA256:BoP/KLS17g+gUuQ7mrCHa9oPPO+MHi/h8WML44iA1dw.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'biowulf.nih.gov,128.231.2.9' (RSA) to the
list of known hosts.
***WARNING***
You are accessing a U.S. Government information system, which includes
(1) this computer, (2) this computer network, (3) all computers
connected to this network, and (4) all devices and storage media
attached to this network or to a computer on this network. This
information system is provided for U.S. Government-authorized use only.
Unauthorized or improper use of this system may result in disciplinary
action, as well as civil and criminal penalties.
By using this information system, you understand and consent to the
following:
* You have no reasonable expectation of privacy regarding any
communications or data transiting or stored on this information system.
At any time, and for any lawful Government purpose, the government may
monitor, intercept, record, and search and seize any communication or
data transiting or stored on this information system.
* Any communication or data transiting or stored on this information
system may be disclosed or used for any lawful Government purpose.
--
NOTE: This system is rebooted for patches and maintenance on the first
Monday of every month at 7:00 AM unless Monday is a holiday, in which
case it is rebooted the following Tuesday. A detailed schedule is
available at http://helix.nih.gov/Documentation/reboots.html
Last login: Thu Apr 17 07:46:21 2025 from hostname
[username@biowulf ~]$
PuTTY
Installation of PuTTY may require administrative privileges. Please consult with your local system administrators regarding installation policies.
Because PuTTY is continuously updated, you should download the latest
version from
http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html.
The download page includes a self contained executable (putty.exe) available under the "Alternative binary files" heading,
and an installer (putty-<version>-installer.msi) available under the "Package files" heading. The installer
will require administrative privileges. For most Windows users, the 64-bit x86: putty.exe under the "Alternative binary files" will probably suffice.
Once PuTTY is installed or downloaded, start PuTTY by double-clicking the icon created on your desktop or use your search bar to locate the executable
Setting up sessions with PuTTY
When starting PuTTY, you will see a dialog box. This dialog box allows you to control everything PuTTY can do. In the 'Host Name' box, enter helix.nih.gov or biowulf.nih.gov.
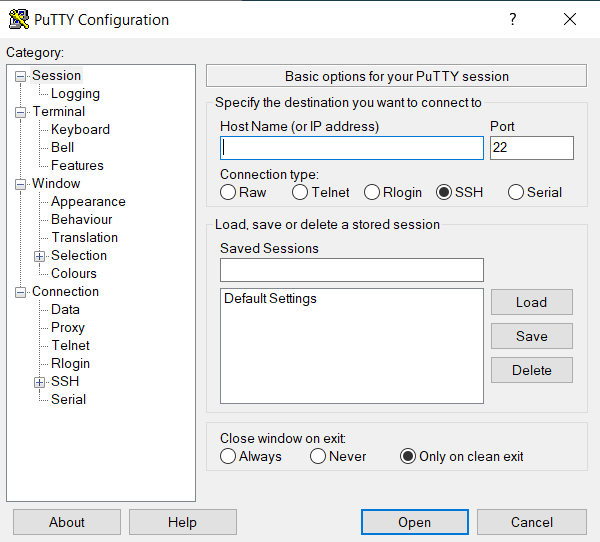
Quick Start
For a quick start, simply type "biowulf.nih.gov" or "helix.nih.gov" into the Host Name field and press the "Open" button.
When prompted for your username, enter your NIH username.
Helpful Suggestions
You don't need to change most of the configuration options, but here are a few suggestions below.Specify your username in the Host Name field
Specifying a username in the host name field will mean you do not need to type your username when clicking "Open". Instead, useyour_username@biowulf.nih.gov or your_username@helix.nih.gov in the Host Name field. Replace "your_username" with your NIH username.
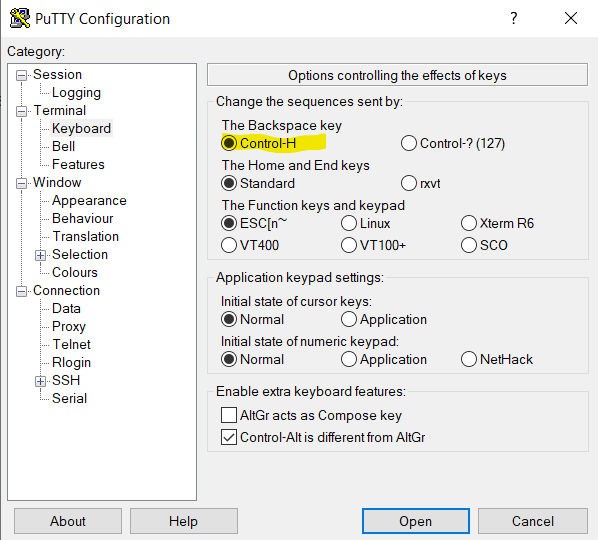
The Backspace Key
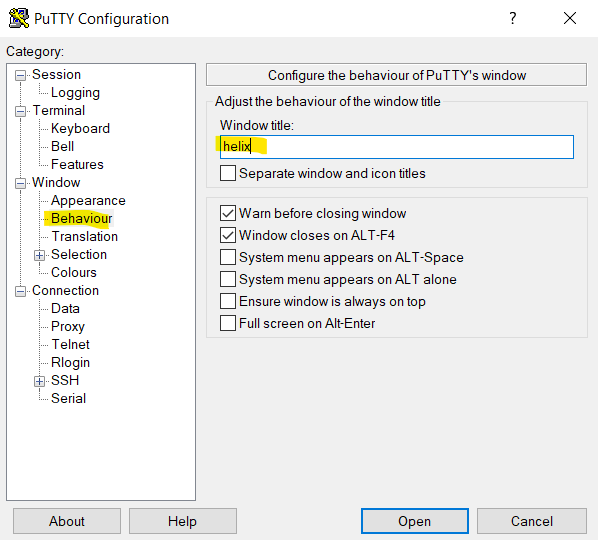
The Window Title
Enable X11 Forwarding
PuTTY can forward the X11 protocol which can be used together with an X11 server on your computer to run graphical applictions. However, we recommend using Open OnDemand for this purpose

After making your configuration changes, be sure to save the session so you will not have to reconfigure PuTTY each time.

When first connecting to a new server, PuTTY will report that the server's host key is not cached in the registry yet. It will present the fingerprint of the host key. If the fingerprint matches one of the fingerprints shown above it is safe to answer "yes" and store the key in PuTTY's cache
Creating icons on your Windows desktop
Right-click the PuTTY icon on your desktop, then left-click "Properties".
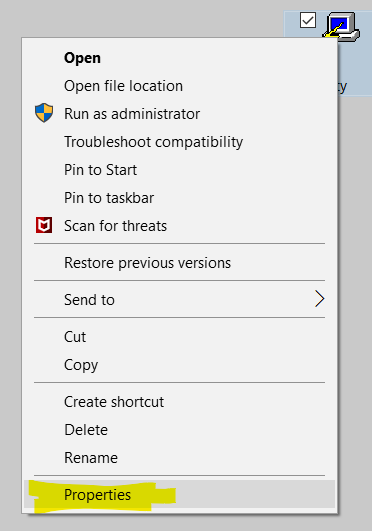
In the "Target" box under the Shortcut tab, type -load "helix" or -load "helix.nih.gov" after putty.exe:
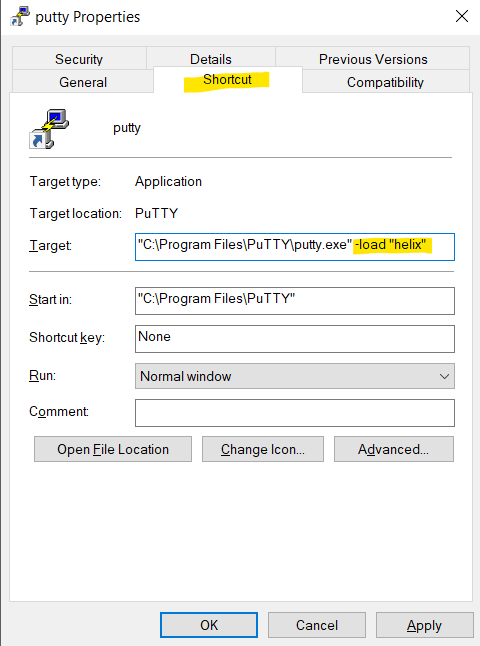
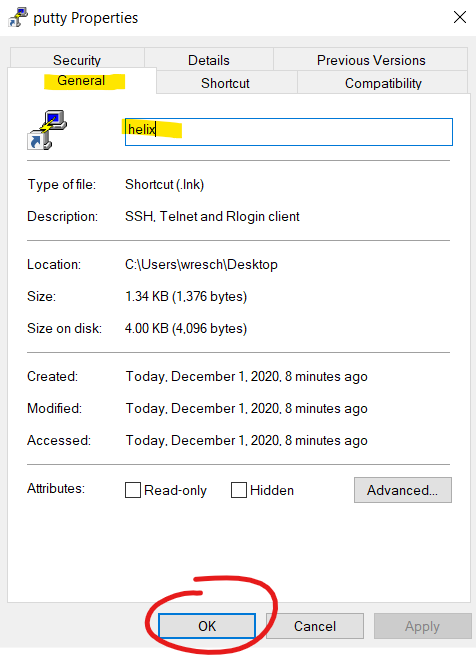
Click on the 'General' tab and change the name from PuTTY to helix, then click the OK button.
Double-click on the helix icon to login to helix
To create an icon for any of the other systems, be sure to make a copy of the helix or PuTTY icon, then change the properties of the copy.
Documentation
For more in-depth knowledge of PuTTY, see the PuTTY Documentation Page
If you wish to use X11 Forwarding with PuTTY on Windows, you will also need an X11 server running. Xming is an X11 Server available on Windows. Download the installer and install XMing into your Documents or other personal folder. XMing must be started before connecting with PuTTY for X11 Forwarding to function.
Graphical connection
Direct access to graphical applications on Biowulf over an SSH connection from Windows is possible, although not supported by HPC staff. Software like MobaXterm can provide this kind of access if desired.